The Triad of Computing Security Includes Which of the Following
The Fourth Amendment c. Vulnerability assessment detection and monitoring c.
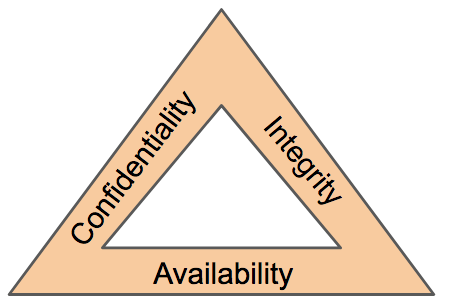
Confidentiality Integrity And Availability The Cia Triad Certmike
Answer Explanation1 There are three sides of triads as vulnerability assessment risk management and computer investigations.

. Vulnerability Assesment Intrusion Response and Investigations. C-I-A triadSecurity triad Confidentiality integrity availability nonrepudiation authentication and auditability. The triad of computing security includes which of the following.
The Central Intelligence Agency. And its clearly not an easy project. Government agency that is responsible for providing national security intelligence to policymakers in the US.
When you hear CIA the first thing you likely think is Central Intelligence Agency which is an independent US. Wesley Chai Technical Writer. Security professionals already know that computer security doesnt stop with the CIA triad.
Vulnerability assessment intrusion response and investigation d. To protect any asset that the company deems valuable. Detection response and monitoringb.
The Third Amendment b. Vulnerability assessment intrusion response and monitoring. Vulnerabilitythreat assessment and risk management network intrusion detection and.
The triad of computing security includes which of the following. Vulnerability assessment detection and monitoring c. Guide to Computer Forensics and Investigations 6th Edition Edit edition Solutions for Chapter 1 Problem 3RQ.
1 Answer to The triad of computing security includes which of the following. Detection response and monitoring b. Vulnerability assessment intrusion response and investigation.
Num1 QA. Detecting a threat and monitoring it is done to ensure the safety of the company. 2 The triad of computing security includes which of the following.
Detection response and monitoring b. Vulnerability assessment intrusion response and investigation. The triad of computing security includes which of the following.
The triad of computing security includes which of the followinga. The triad of computing security includes which of the following. List two organizations mentioned in the chapter that provide.
Vulnerability assessment intrusion response and investigation. Vulnerability assessment detection and monitoringc. Vulnerability assessment detection and monitoring.
These three together are referred to as the security triad the CIA triad and the AIC triad. All these sides represents a department for computer security and they work in coordination to achieve it. Vulnerability assessment detection and monitoring.
Detection response and monitoring. Most IT security practices are focused on protecting systems from loss of confidentiality loss of integrity and loss of availability. The triad of computing security includes which of the followinga.
ISO-7498-2 also includes additional properties for computer security. Police in the United States must use procedures that adhere to which of the following. Which of these are common types of digital crime.
The triad of computing security includes which of the followinga. Access control systems perform identification authentication and authorization of users and entities by evaluating required login credentials that can include passwords personal identification numbers PINs biometric scans security tokens or other authentication factors. Vulnerability assessment detection and monitoring c.
Choose all that apply aharassment bcyber-stalking cembezzlement dbattery. The triad of computing security includes which of the. Vulnerability assessment intrusion response and monitoring Ans.
32The triad of computing security includes which of the following. However what many people dont realize is that the CIA Triad actually stands for. A Detection response and monitoring b Vulnerability assessment detection and monitoring c Vulnerabilitythreat assessment and risk management network intrusion detection and incident response and digital investigation.
False The triad of computing security includes which of the. The First Amendment d. The model is also sometimes referred to as the AIC triad availability integrity and confidentiality to avoid confusion with the Central.
Vulnerability assessment detection and monitoring c. Guide to Computer Forensics and Investigations with DVD 5th Edition Edit edition Solutions for Chapter 1 Problem 3RQ. Detection response and monitoring b.
Confidentiality integrity and availability also known as the CIA triad is a model designed to guide policies for information security within an organization. This article provides an overview of common means to protect against loss of confidentiality integrity and availability. Detection response and monitoring.
The triad of computing security includes which of the following. An unauthorized person accesses a data item. Course Title ICT.
Detection response and monitoringb. And that is the work of the security team. Vulnerability assessment intrusion response and investigation d.
None of the above Fourth Amendment. The triad of computing security includes which of the following. Vulnerability assessment intrusion response and monitoring.
Then print the sum of those numbers. Vulnerability assessment intrusion response and monitoring. Vulnerability assessment intrusion response and investigation d.
Vulnerabilitythreat assessment and risk management network intrusion detection and incident response and digital investigation d. An unauthorized process or program accesses a data item. Detection response and monitoring b.
Hint -- Copypaste the following code then just type code where the questions marks are to finish the code. 1docx - Digital forensics and data recovery refer to the.

The Cia Triad In Cryptography Geeksforgeeks

Information Security Principles What Is The Cia Triad


Comments
Post a Comment